Windows provides a way to include an application handler into a system hook chain; this can be used to implement, for example: If the second point sounds a bit obscure, well… that’s exactly the case we needed to improve. Our software implements an integration system that operates not only at protocol level (IPC) but also […]

Analyzing a 0xE06D7363 exception
Sometimes it happens we have to analyze dumps of our application: it’s a mixed .NET/C/C++ software, so the legacy libraries can trigger unhandled exceptions that cause the process to crash. In most of these cases either through the internal minidumper or thanks to the WER, the user is able to send us the core dump, […]
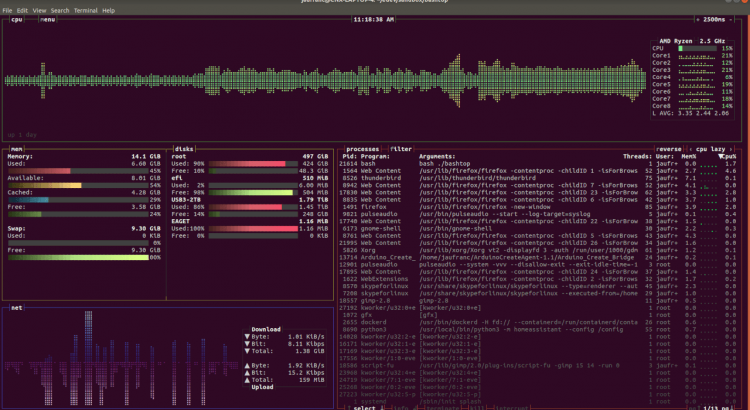
The cost of performance monitoring
When writing software (in particular applications that can make intense use of the system resources, such as CPU, GPU, memory) it can be helpful to have a way to monitor how things are going, and this includes not only how the application is behaving but also if the entire system is sane and responsive. In […]
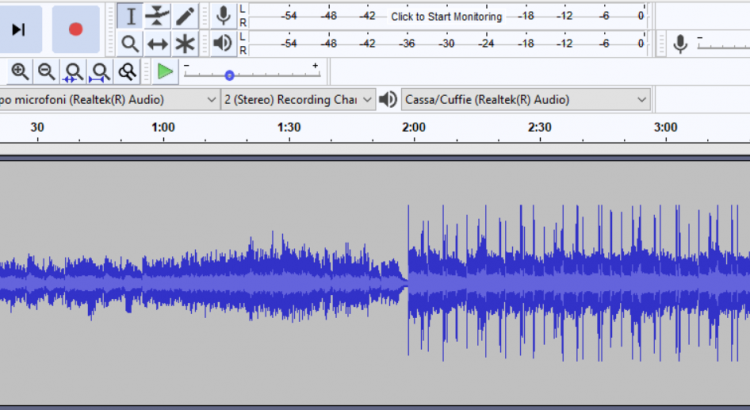
Windows Core Audio API
Whoever has used advanced audio apparels knows that the most used driver is the ASIO one: quite commonly, each audio interface is provided with a proprietary implementation of the ASIO specifications and the driver is generally used from within the Digital Audio Workstation or other applications that are able to stream through this protocol. ASIO […]

Humble CPU Monitor
As a developer, one of the many concerns I have when I write and test software is “how much CPU does this thing use?” – and in Windows there are some ways to keep an eye on this, depending on the level of details you’re interested in. For example, the GetProcessTimes function is useful to […]

Kerberos
Kerberos is an authentication protocol originally developed by MIT and implemented by various vendors and systems; probably its best description is in the first paragraph that can be found in the MIT Kerberos site: Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. A […]

WPF and handles
There’s a famous article from Microsoft that says “Give me an handle, and I”ll show you an object“, dated July 15, 1993. There are a lot of Windows objects that can be retrieved using a handle, mainly GDI and USER objects but also Kernel objects are identified by handles – for example, the HeapCreate function, used […]
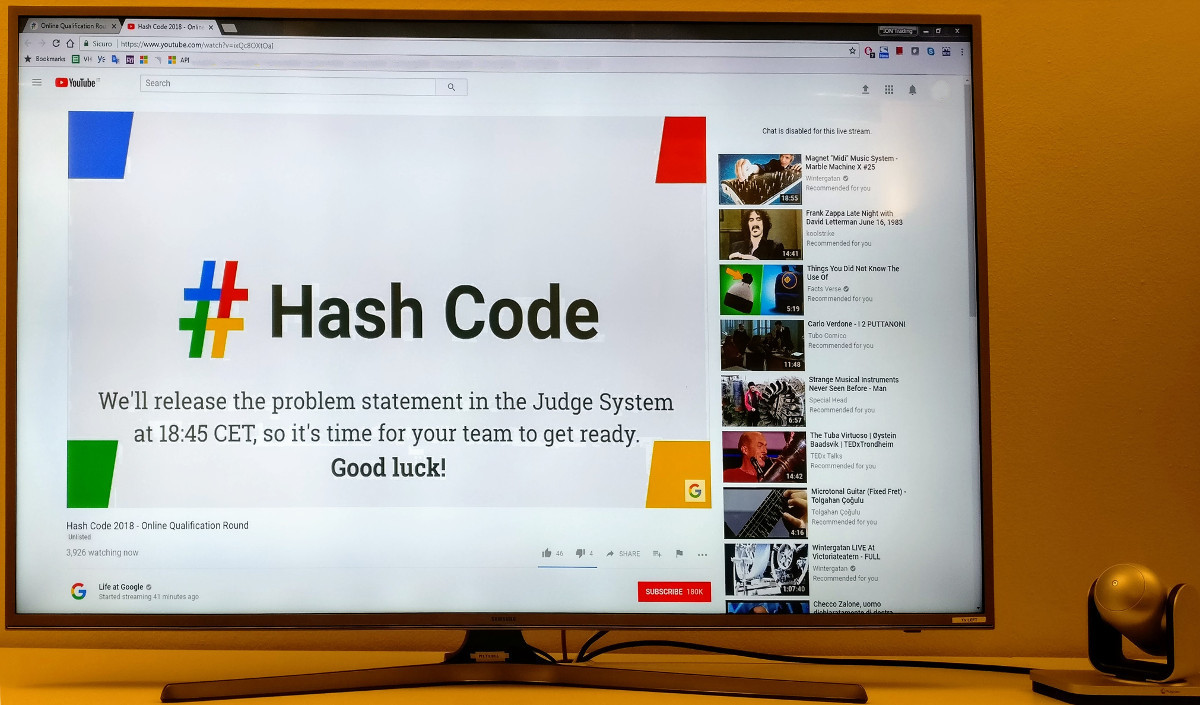
Google Hashcode 2018
For the first time, this year, me and three colleagues of mine participated to the Google Hash Code challenge; this year the problem was open to Europe, Middle East and Africa: in the end 4856 teams has participated to the game. We knew we didn’t have too many chances to get a good result due […]

Interop between managed and legacy code
It’s quite common and easy to use legacy code from within a piece of managed code but sometimes it comes in handy to call managed code from legacy code. To do so, we’ll write a C++ class which will actually use a managed object but that has a plain, legacy interface. The first thing to do is to […]

How to build/install gcc/g++ from sources on a Raspberry Pi
The easiest, fastest and painless solution is using a pre-compiled package: some apt-get install stuff after added the proper repo of the distro generally does the trick. But fortunately GCC/G++ are always in progress tools and it is useful to be able to align to the most recent version autonomously.
